Perimeter Sensing using YOLO
Perimeter sensing goes beyond motion detection by understanding context, object interaction, and zone awareness using computer vision to deliver reliable, real-world security intelligence.
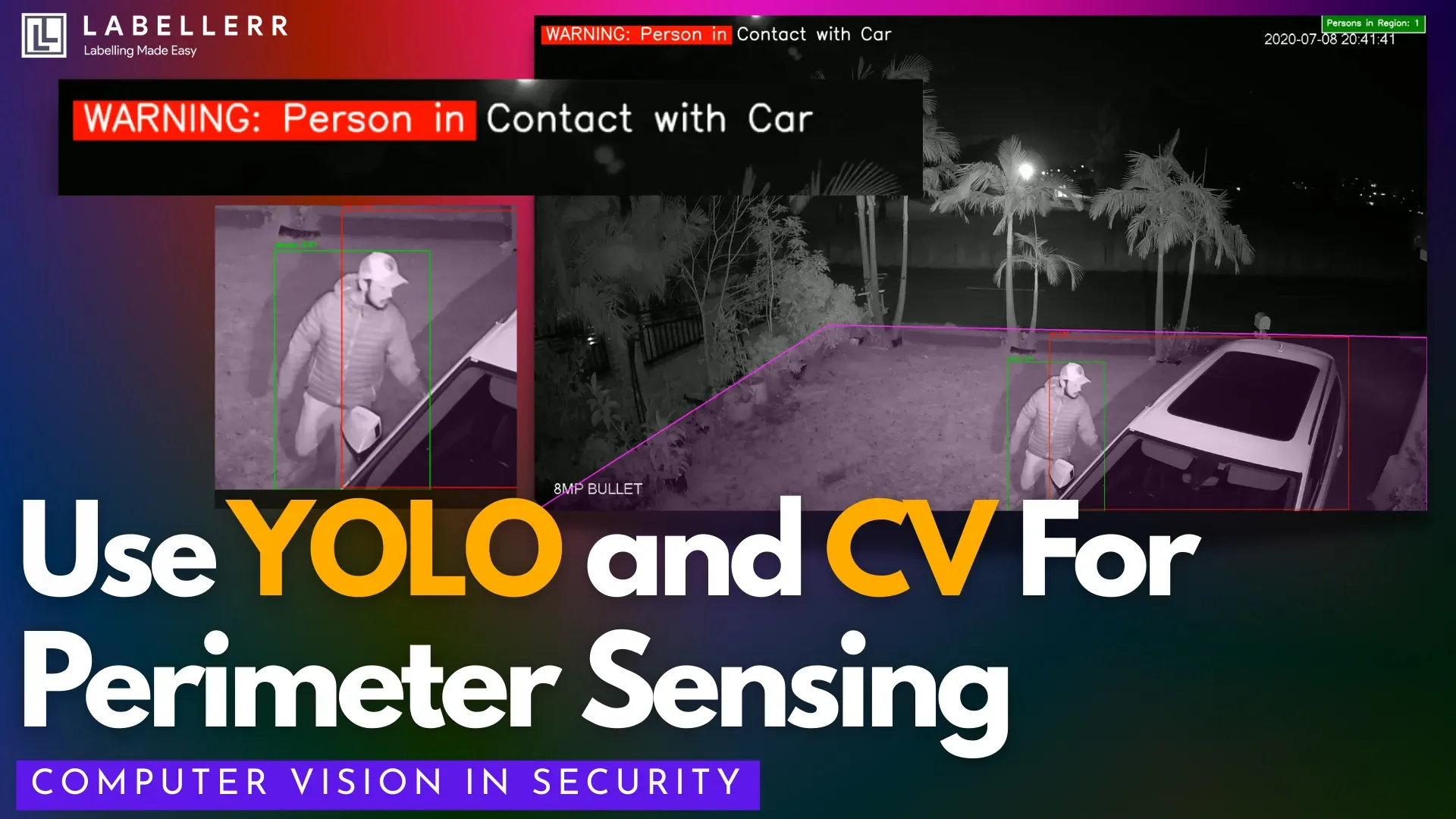
In real deployments, perimeter violations are rarely about sudden motion, they are about context. A person may loiter near a boundary, a vehicle may stop within a sensitive zone, or brief contact may occur before any clear breach is visible.
The opening inference illustrates this clearly: detection alone is not enough; understanding interaction is what matters.
Modern perimeter sensing systems use computer vision to combine object detection, region awareness, and temporal logic. By defining virtual perimeters and reasoning over object proximity and contact events, these systems can distinguish benign movement from actionable risk, something traditional motion sensors consistently fail to do.
In this blog, we explain perimeter sensing using clear visual inference and grounded implementation logic, focusing on reliability, explainability, and real-world deployment constraints.

Perimeter Detection in action
What is Perimeter Sensing?
A smart surveillance system is a sophisticated network of devices whose primary objective is to "detect and respond to the presence of unwanted individuals or objects within restricted zones."
These systems are crucial for protecting a wide range of environments, including government buildings, factories, warehouses, financial institutions, and military bases.
While cameras are foundational, a modern security ecosystem can include several types of integrated technologies.
• Perimeter Security Robots: These are autonomous machines capable of patrolling and monitoring vast areas. Equipped with 2D and 3D cameras, they overcome the limitations of stationary monitoring and add a dynamic layer of protection, especially in conditions like nighttime patrols where human surveillance may be challenging.
• Drones for Perimeter Security: As an advanced form of aerial surveillance, drones offer a flexible bird's-eye perspective, providing strategic viewpoints that are essential for preemptive threat assessment. As noted by security experts, drones are heavily used by law enforcement and the military to gain intelligence on potential threats, allowing for more informed and proactive decision-making.
• Surveillance Cameras: Serving as the foundation of security systems, cameras are strategically placed to oversee secured areas. Modern cameras provide high-resolution images, 360-degree coverage, and features like infrared and thermal sensitivity for effective night vision, ensuring continuous surveillance in all conditions.
While robots and drones provide dynamic new capabilities, the strategic placement and intelligent operation of surveillance cameras remain the cornerstone of a truly effective modern security posture.
How Computer Vision can help in it?
Artificial intelligence is the critical element that transforms a standard camera into a "smart" one. By analyzing video streams in real time, AI provides capabilities that were previously impossible, turning surveillance into a proactive defense mechanism.
• Object Recognition: AI can distinguish between different objects. It understands the difference between a person, an animal, or a vehicle, which allows the system to make more accurate threat assessments and reduce false alarms.
• Deep Learning (DL): This allows the system to get smarter over time. By learning from its experiences, the camera's detection skills gradually improve, making it better at identifying potential dangers with each passing day.
• Automation of Security Tasks: AI can automate routine monitoring tasks, such as tracking movement in a specific area. This frees up human personnel to focus on higher-level decision-making and response.
• Enhanced Threat Detection: AI provides an extra set of tireless eyes that never get fatigued. It can detect subtle intrusions and anomalies that a human operator might miss, significantly strengthening the overall security posture.
Inference Result using Computer Vision
This is a result inference of perimeter sensing in real time.
Here, detections are then used to determine whether a person have entered defined zones of interest around a perimeter and whether meaningful interactions occur within those zones.
The inference result highlights not just raw object presence but also spatial relationships between objects and the perimeter boundaries, triggering alerts or flagging events when an object crosses or interacts with a perimeter region.
Conclusion
The paradigm shift in perimeter security is not merely about adding new hardware like drones and robots; it is about creating a unified ecosystem where intelligent cameras serve as the central nervous system.
These systems offer continuous, cost-effective, and comprehensive protection by not only seeing but understanding the environments they monitor. By moving from a reactive to a proactive model, they are fundamentally changing how we protect our most critical assets.
As these security systems become more intelligent and autonomous, what is the next frontier for protecting our most critical spaces?
FAQs
How is computer vision–based perimeter sensing different from traditional motion detection?
Traditional motion sensors react to pixel changes, while computer vision understands objects, zones, and interactions, reducing false alarms and improving contextual accuracy.
What types of environments benefit most from perimeter sensing systems?
Critical infrastructure such as factories, warehouses, government facilities, campuses, and military installations benefit most due to large areas and high security risk.
Can perimeter sensing systems reduce false positives in real deployments?
Yes. By combining object detection, spatial awareness, and temporal logic, these systems distinguish normal activity from genuine threats more reliably.
Simplify Your Data Annotation Workflow With Proven Strategies
.png)